Hacking, phishing, data theft, identity theft, fraud—and the list goes on—sounds scary, especially if you are clueless about how to protect yourself. It can be dangerous in terms of exposing your private data or getting defrauded, but with some simple precautions we can navigate the digital world safely. Today I will talk about Phishing—a very common form of online fraud which unsuspecting users very easily fall prey to.
“Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details (and, indirectly, money), often for malicious reasons, by disguising as a trustworthy entity in an electronic communication.” – Wikipedia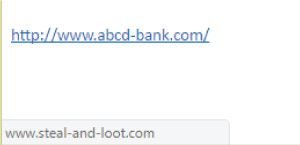
The word “Phishing” sounds similar to fishing, and for a good reason. In fishing a bait is put in the water for the fish to bite. Some incentive is given to the user to click on a link or perform some other action in order to get sensitive information. The most common examples of this are emails which claim to be from bank websites or mails talking of unclaimed fortunes waiting to be claimed. So, too, links which appear to be for some shopping website sale or lucky dip.
How do we identify these traps? Well, we need to keep a few points in mind:
- The “from address” in a mail can seem to be from a genuine source, but may not be so. Just as we can write a wrong ‘From Address’ on an envelope, so can the ‘From Address’ be changed on an email or message. Banks don’t ask for sensitive information by mail. So don’t give It, nor click on the mail claiming to take you to the bank website.
- Always check the actual link address in a mail or webpage which is doubtful. The text displayed on the screen may not be the actual link. To check the link, hover over the link with the mouse pointer, and the link will appear at the bottom of the browser or in a small pop up in some other applications. Alternatively, you can right click (careful: not left click) the link and select “copy link” (or an equivalent) and paste it in a text editor and verify it.
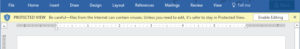
- Do not open attachments from untrusted sources. Files with extensions .com, .exe, .bat, .scr and .msi can be very dangerous. Even Microsoft Office documents (.doc, .docx, .xls, .xlsx, .ppt, .pptx) can contain computer instructions or commands called macros which can be exploited by malicious parties. Microsoft Office opens documents downloaded from internet by default in ‘Protected View’ with execution of macros disabled. This is indicated by the yellow bar on top saying ‘Protected View’. Do not switch to non-protected mode unless you are sure the document is really safe.
- Understand the domain address. As an example, look at the following link:
http://www.amazon.big-sale.com
You might think this is related to some sale on amazon.com, but in reality this link is not related to amazon.com. You see, we have to read from right to left for this part of the web address. The ‘.com’ or ‘.org’ being the top-level domain. The link in this case is for the site big-sale.com and which has created a subdomain called ‘amazon’ which is not related to amazon.com. So you need to look at the name that appears just before the ‘top-level domain’ that is .com, .org, .net etc. That is the actual website. So in this case the actual website is big-sale.com. So if the link is trying to appear like something that it is not, don’t click it, no matter how tempting it looks.
Please note that these things can happen via Whatsapp / SMS or other instant messaging apps also.
Knowing these dangerous steps can help us stay safe while using modern technology to your advantage.
-Mithun Davis, is a Jesus Youth leader and software engineer
To subscribe to the magazine Contact Us





